Intro
Years ago, when I was interviewing for my first legal job, I remember meeting with a partner in a large firm the day after a viral news story about a trust accounting scam that had affected that partner’s firm. Essentially, the scam involved an attorney’s acceptance of a matter, with a significant retainer being paid with what is later discovered to be a fraudulent check. Then, the supposed “client” within a day or two terminates representation and demands refund of their retainer - which is satisfied promptly (as required by ethics rules) using a legitimate check drawn on the firm’s trust account. Later, the fraudulent check bounces, leaving the firm holding the bag.
I won’t mention the firm or amount involved here, as it was very significant, but needless to say I did not get a job with that firm. So, in true butterfly effect fashion, I am here today writing about some recent scams and phishing attempts I have seen - in part due to the past effect of a legal scam on my employment search.
E-mail Spoofing
I routinely start my day sifting through e-mails in my inbox that have one of these flavors:
One purportedly from the “managing partner” of one of the firms I work with - sometimes addressed to me by name - asking me to contact them as soon as I get in. The problem is that, while the e-mail has the managing partner’s name, the underlying e-mail address does not use the domain name of the firm in question.
An e-mail addressed to me as “Counselor” asking me if I can assist with the preparation of a purchase and sale agreement.
An e-mail notifying me that our benefit plan, or Microsoft 365 subscription, or some other data service has experienced a change - commanding a “response” that I click the link so helpfully embedded in the e-mail and enter my credentials to address the change.
An e-mail from a legit client, usually with some mailing purporting to be from a state Secretary of State’s office asking them to submit a form and pay a fee for their annual renewal or from a Clerk and Recorder’s office asking them to pay a fee for a copy of their vesting deed. The problem is that the form itself does not go to the Secretary of State or Clerk and Recorder, but goes to some artfully named “Corporate Records Department” entity that in fine print holds itself out to be a third party vendor assisting with filings for a “fee.”
These scams are nothing new. It is hard for me to remember a week in recent times that I did not see at least one of these in my e-mail inbox.
But, I recently saw something even more nefarious and personal. I was forwarded an e-mail that appeared to be spoofed from me, instructing a manager or office administrator to change my direct deposit info. Obviously this was not something I had instructed, but it was only when someone e-mailed or called me to confirm that I found out about the spoofing/phishing attempt.
Long story short, a delightful drawback of having an e-mail address publicly listed on a firm website is the inevitable exposure to these types of attempts. Likewise, having business entity info publicly listed on a Secretary of State website or a county assessor’s website can lead to these and other types of issues.
With the looming beneficial ownership compliance deadlines, we are also seeing an uptick in scams.
Beneficial Ownership and Form 5102?
A recent question came across my desk that involves beneficial ownership reporting for purposes of complying with the Corporate Transparency Act. Now, you should note that beneficial ownership reporting is done directly to FinCEN, through online data entry (although room is carved out for API interfaces with the portal for certain outside vendors to collect and report beneficiary ownership information).
If you search for beneficial ownership information reporting, luckily the top result is a legitimate link to the FinCEN portal, where this information is reported at no cost:
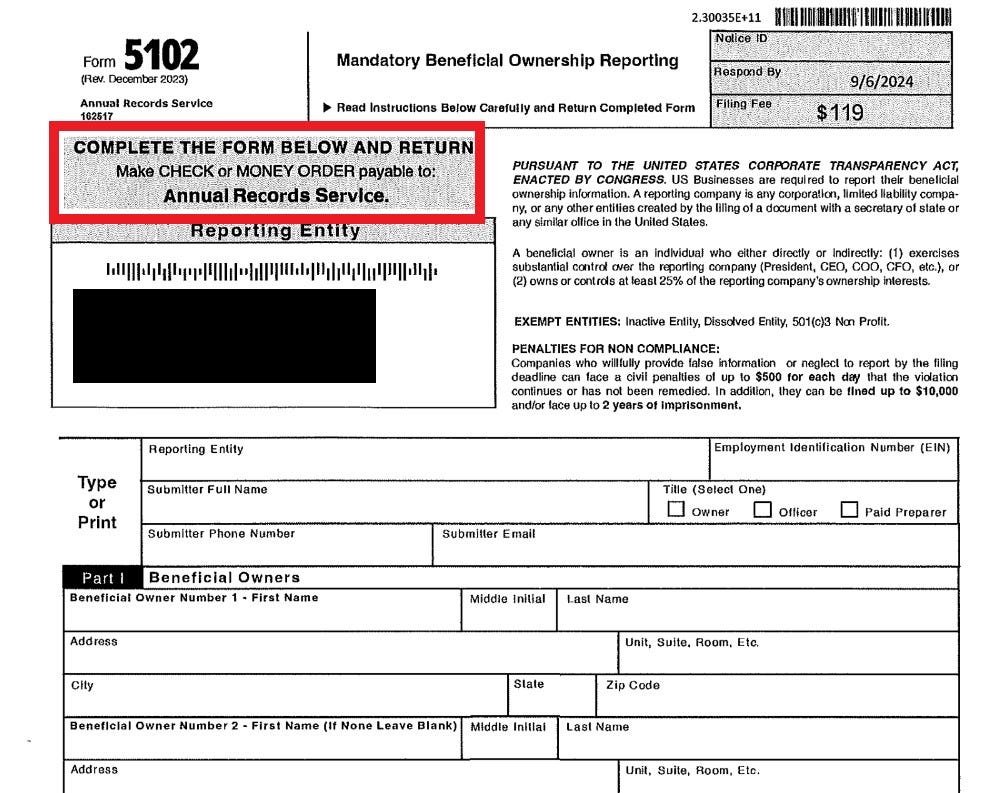
Unfortunately, there is a new scam going around through which an entity appears to be phishing for information, and an illegitimate fee, through a somewhat official-looking “Form 5102:”
Importantly, as seen in the red box, this is prompting for payment of a fee to “Annual Records Service” instead of FinCEN (who does not charge a fee). What I did not post is the disclaimer at the bottom, following some threatening language about accuracy and penalties of perjury, stating, “Your signature is your acceptance for The Annual Records Service to act as your paid preparer to file this BOI on your behalf.”
In a world where clients are hesitant to submit their information to FinCEN to begin with, this seems like an even bigger risk - the disclosure of information to a non-government private entity. Which raises a bigger question… what do you do if you discover, for example, that an employee in your organization mistakes this for a legitimate form and submits it? That is a subject for another time, and the good news is that this form is not prompting for (1) a copy of a government-issued ID or (2) the number of that ID (both of which are required in a BOI report).
What if, however, sensitive information like a social security number (SSN) were to be reported to someone other than the IRS?
EIN Scams
I have witnessed first-hand the submission, by legal support staff, of an application for an employer identification number (EIN) to the wrong vendor. This was scary, because (1) a fee was charged by the vendor ($250 per application as I recall), and (2) the client’s SSN was disclosed to said vendor - resulting in the need for credit monitoring and locks by the client (not to mention egg on our face).
The application for an EIN is a free application on the IRS website. Yet, if you search for EIN online application, you find “sponsored” vendors at the top of the results list:
You can tell by the web address that “irs.gov” does not show up, but anyone lacking knowledge or simply acting in a rush can miss that. And, it means turning over data (including an SSN) to someone who might not be identifiable, with the added cost of paying an unnecessary fee for them to act as a “dedicated specialist” to review and determine the accuracy and completeness of your information as seen below:
I’ll let you draw your own conclusions about how catastrophic the use of such a seemingly-legitimate service can be.
Conclusion
In today’s modern wealth transfer practices, we are pressed for time. It is easy for us, and for our support staff, to get in a rush. It is also easy to assume that you would not get fooled by a scam like this. But, it happens every day to people who thought they were too intelligent to fall for it.
And, while there are tons of resources out there cautioning us not to click on links in e-mails, and not to enter our login credentials or bank account information, it is one thing to know this in theory yet quite another to see how legitimate some phishing e-mails can look.
Lest you think I am judging you, I am not. I, too, have fallen for this - and it just happened to be a matter of timing. Years ago, I had filed an online dispute with my bank about a charge on my account. Around this same time, I got an automated call stating that a fraudulent charge had been spotted and that I needed to input my debit card number to shut down the card. Given the timing, I assumed this call was from the bank. It was not. Fortunately, I called the bank and ascertained that I had fallen for a spoof which allowed them to legitimately close the card before more damage could be done.
All that said, this can happen to the best of us. At the beginning of the story, it happened to a sophisticated partner at a high-end law firm. For the EIN, it happened when support staff went unsupervised with an assumption that they knew how to complete this task. At the end of the story, it happened to me.
So, if you spot spoofs and scams you would like to share, feel free to reach out. This newsletter is not just about the technical. It is about covering yourself in a fast-moving digital world where bad actors can take advantage of your willingness to engage in a transaction that is not face-to-face. And, with the onset of AI, these issues are sure to compound.